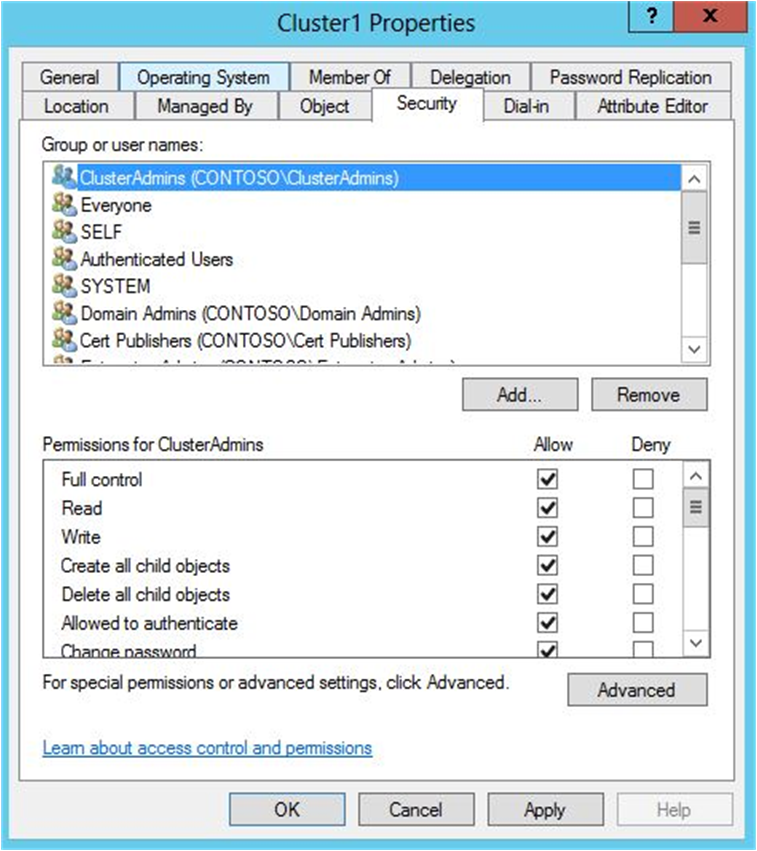
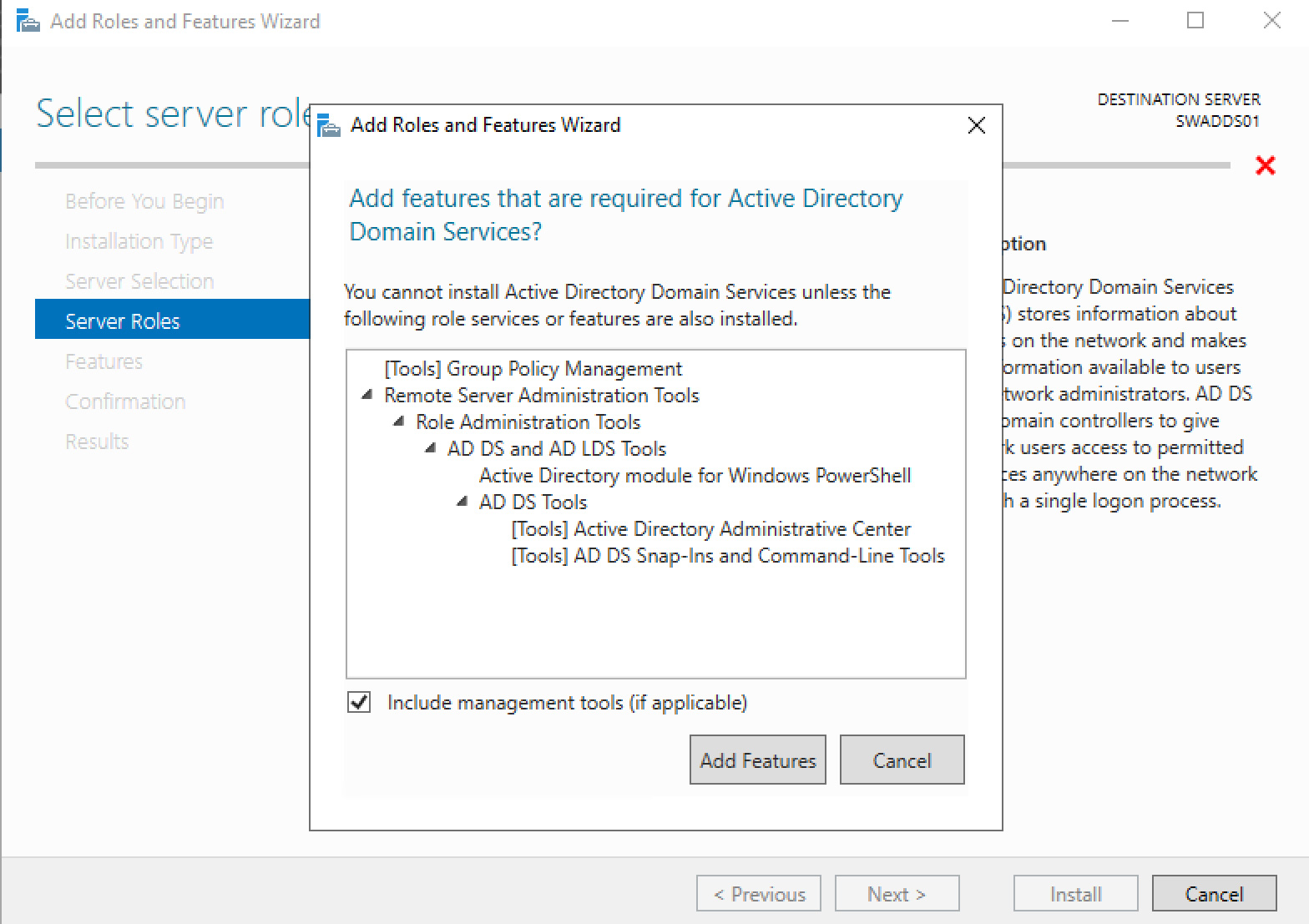
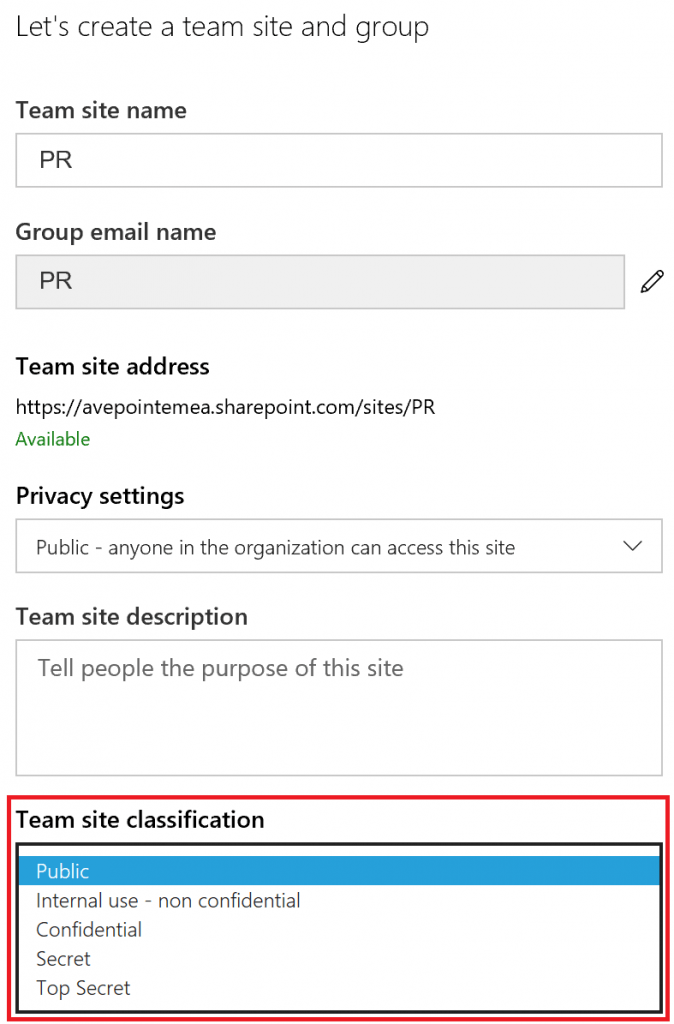
It s important to regularly take stock of which employees have access and permission to which resources.
Active directory security group naming best practices.
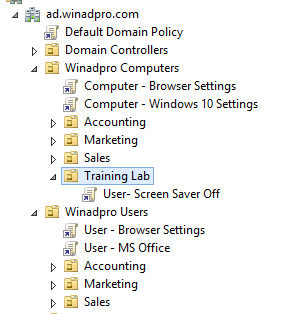
Nesting helps you better manage and administer your environment based on business roles functions and management rules.
As the table above illustrates a group can be a member of another group.
Best practices for naming an active directory domain.
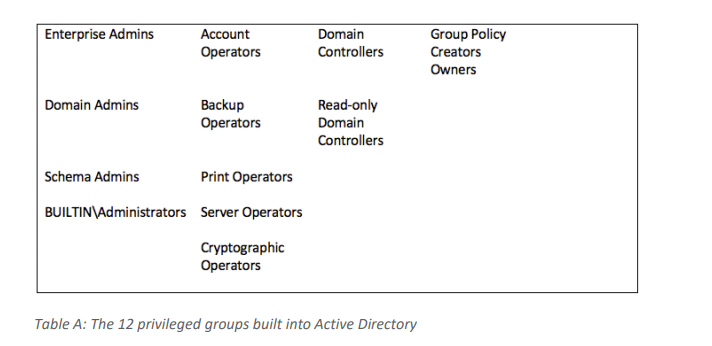
Clean up the domain admins group.
One small change could lead to major issues and impact critical business services.
Leverage group naming prefixes.
Best practices for securing active directory.
I also explain why i think solarwinds access rights manager is the best tool available on the market today to help support your ad security efforts.
Active directory plays a critical role in the it infrastructure and ensures the harmony and security of different network resources in a global interconnected environment.
If there is not a suffix on the group name then read write is assumed.
In this guide i will share my tips on securing domain admins local administrators audit policies monitoring ad for compromise password policies vulnerability scanning and much more.
Dns is the domain naming system used to translate names into network ip addresses.
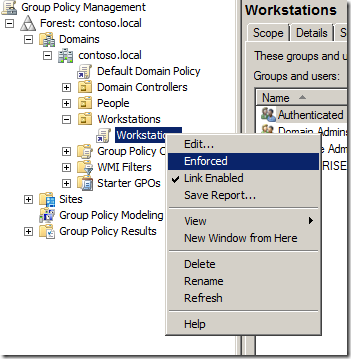
It is best to plan and test any changes to group policy.
This process is called nesting.
In this article i define what exactly active directory security groups are including their functions and scope before sharing my quick guide to active directory security groups best practices.
In addition to group nesting management tips there are also many things to keep in mind when it comes to managing your security groups.
Suffix used for group naming to annotate rights given via group membership 1.
We know that many organizations like to enforce a group name prefix.
Our first best practice.
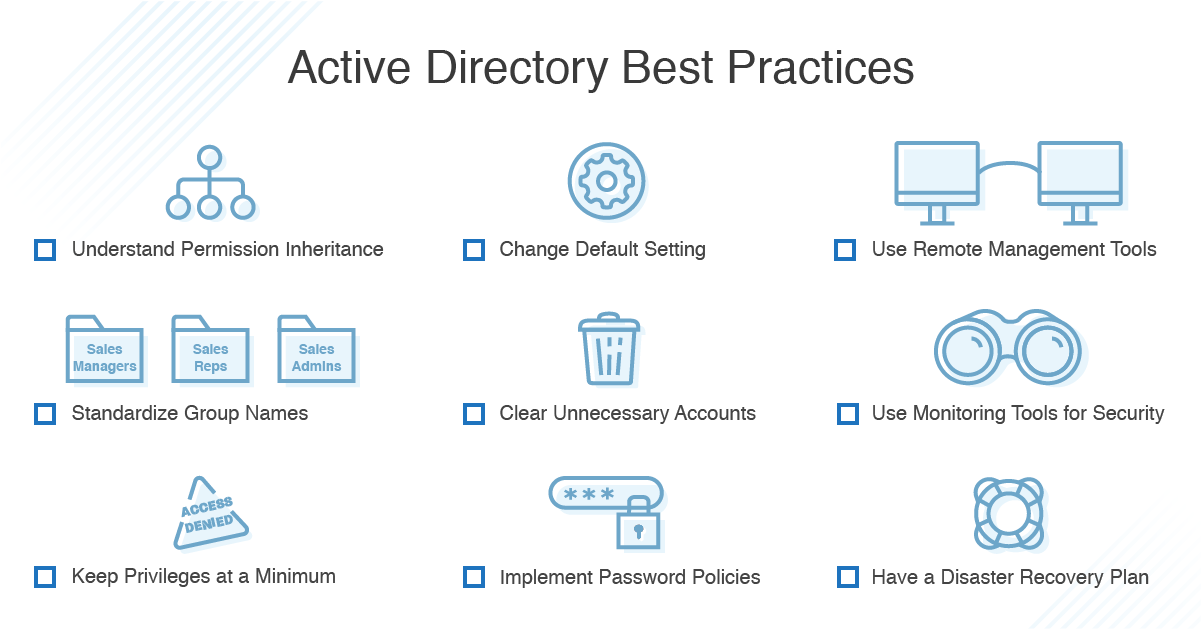
This is the most comprehensive list of active directory security tips and best practices you will find.
2 minutes to read 2.
When planning for a new active directory ad or upgrade ad or merging ad one of the topics that will get on the table is planning dns.
Active directory nested groups best practices.
What policies go into place now should remain in place and only be added upon.
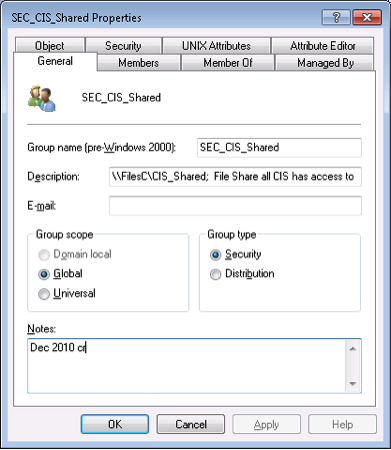
Explicit information on the group s use should also be reflected in the description and notes field of the group object in active directory ad.
The methods discussed are based largely on the microsoft information security and risk.
Active directory security groups best practices.
Inside out security blog active directory best practices for naming an active directory domain.
Understand who and what.
Most employees don t need.
Whatever rules you are to implement be consistent over the life of the directory.